James “Evil Jim” Ulrich and Mary Donnelly are two long-standing members of the Binghamton musical drama troupe Summer Savoyards, which has been putting on plays in various local venues since 1961. The Savoyards’ latest production of the beloved dark comedy “Arsenic and Old Lace” will be hosted in the Bundy mansion in downtown Binghamton on the first two weekends of April, and Jim and Mary have been building set pieces for it in the wood shop at the Makerspace!
Summer Savoyards chose to put on “Arsenic” because its darkly hilarious story appealed to the Savoyards’ executive board as well as several regular participants in the Savoyards’ productions. Savoyards’ main focus has traditionally been recurring adaptations of various Gilbert and Sullivan plays, but everyone involved felt like trying to adapt something different, and to make use of a new venue in the Bundy mansion annex (in cooperation with some acquaintances there who wanted to promote Bundy as an events venue). Mary volunteered to be the play director, Jim volunteered to take charge of set design and construction, and everyone set about preparing for the show.
Mary wanted to have the show provide a more immersive than usual experience with respect to the audience, both for the sake of providing a fresh take on the play and because of the spacial limitations of the venue at Bundy. As such, Jim set about creating a seating layout for the venue which allowed for a reasonably sized audience to sit within a space arranged with some minimalistic set pieces designed to invoke the feel of a late Victorian living room (i.e., the set of the play), along with several pieces of Victorian furniture (a love seat, a china cabinet, etc.) sourced from Savoyards participants. Jim created or modified designs for several mock door and window frames in the modelling program SketchUp with elaborate detailing reminiscent of the Victorian era, as shown in the screenshots below, based on various Victorianesque design ideas he found through online research. Once he’d created and refined these designs, based on feedback from the other members of Savoyards with respect to physical size and layout, he printed them out with their corresponding bills of materials and cut lists, and took them to the TCMS wood shop to build them.
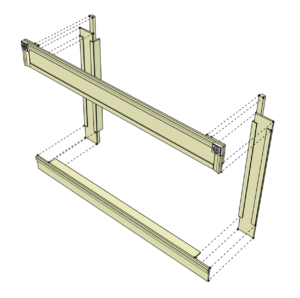
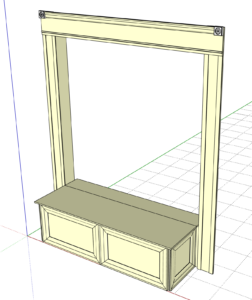
The Makerspace has been used by Jim for building set pieces for past Savoyards productions, but this production involved the largest utilisation of the wood shop for building set pieces yet. Jim, with the help of Mary, Amanda Truin, Eric Adler, and a few odd volunteers, had to build a full padded window seat with a window frame, five additional window frames to be suspended from the ceiling (including one created specifically cover a whiteboard in the annex), and several mock doorway frames. They had $500 to purchase materials to build these set pieces (plus a few additional material donations from Jim), and five weeks to build everything using the tools at TCMS plus a few additional ones provided by Jim. These tools included a table saw and sawhorses, a router, a screw gun, a pneumatic stapler, a multitool, a body grinder, a jigsaw, a chop saw, and various paintbrushes.


Most of the set pieces were built according to the original SketchUp designs, but there were a few modifications made along the way for various reasons. For example, the window seat’s lid was given an additional layer of 1/2” plywood to strengthen it, as various people would be sitting on it throughout the play and the original lid was deemed insufficiently rigid. This lid’s hinges were also extensively modified in several ways to make them squeaky for effect, including treating them with acid and a degreaser, having their pins hammered further into the hinges than typical, and leaving one end of the hinge looser than the other so that excessive flexing would occur. Jim further decided to modify the lintels on the door frames by adding 3/4” pine routed into strips for edge moldings, in addition to the existing frame moldings, to make them even more fancier. Final adjustments were made to the constructed set pieces to accommodate their mounting places in the venue (e.g., providing surfaces for clamps to be fitted to hold the set pieces in place). Finally, long-time Savoyards seamstress Julia Adams volunteered to build a cushion for the window seat and curtains for the window frames.


These set pieces are currently installed in the Bundy museum annex, and you can see them in person on the first two weekends in April when the Savoyards company puts on “Arsenic and Old Lace”! As well as the TCMS members and friends already named, long-term Makerspace members Gary Alan Dewey and Leslie-Morgan Frederick are playing two different roles in the play itself. Come and check it out!



https://www.summersavoyards.org/events
Picture credits:
All photos and drawings are provided and owned by “Evil Jim” and Mary Donnelly.