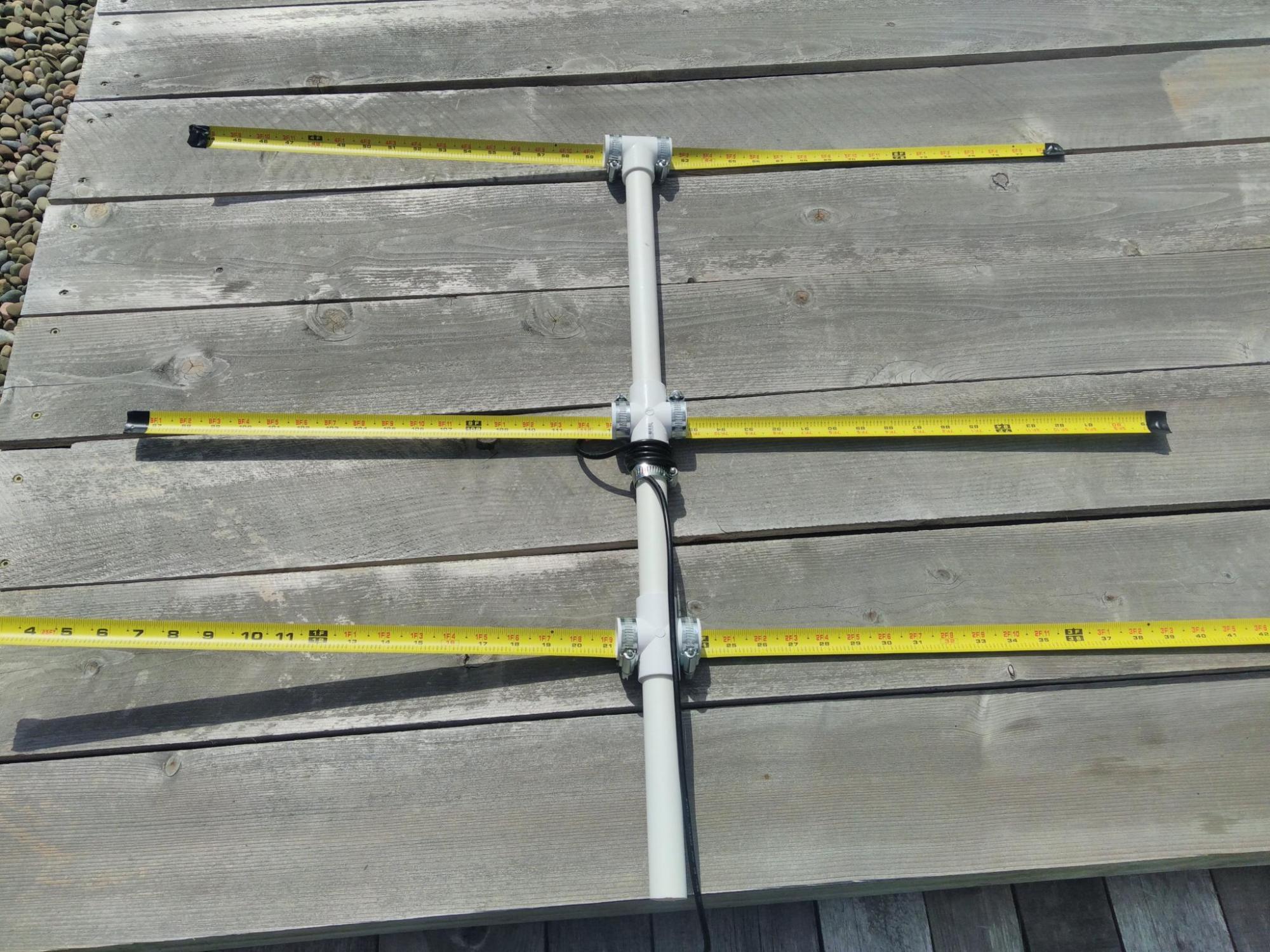
On June 29th., 2019, four members of Triple Cities Makerspace launched, tracked, and recovered a high-altitude balloon.

The balloon used was a 600-gram weather balloon filled with around 100 cubic feet of helium.

The payload consisted of: an HD video camera, an APRS radio transmitter to transmit GPS and altitude data, and a Slow Scan TV transmitter.

The APRS (Automatic Packet Reporting System) transmitter module was supposed to send live GPS coordinates and altitude information on the frequency of 144.390 MHz to any listening I-gates (radio internet gateways) for the duration of the flight.
The Slow Scan TV system consisted of a Raspberry Pi Zero with a Pi camera and a digital to analog converter sound card. The Pi was set up with a Linux daemon script to repeatedly snap a photo, convert it to a Martin-1 Slow Scan TV audio file, then play that file out through a radio transmitter. This would allow us to send live photos during the flight to amateur radio listeners all over the Northeastern region of the United States!
Both of these systems were tested before being assembled and incorporated into the balloon payload container, but both systems experienced problems during the first half of the flight, as the balloon ascended to its peak altitude with the payload. The APRS transmitter was “stuck on” and sent a non-decodable signal for the duration of the first half of the flight, and the SlowScan TV system’s scripted repetition delay of 1 ms ended up providing insufficient time for the camera to adjust for sun saturation, as the first half of the mission the system sent “green” frames.
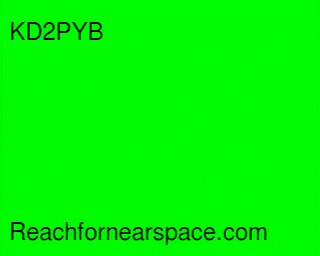
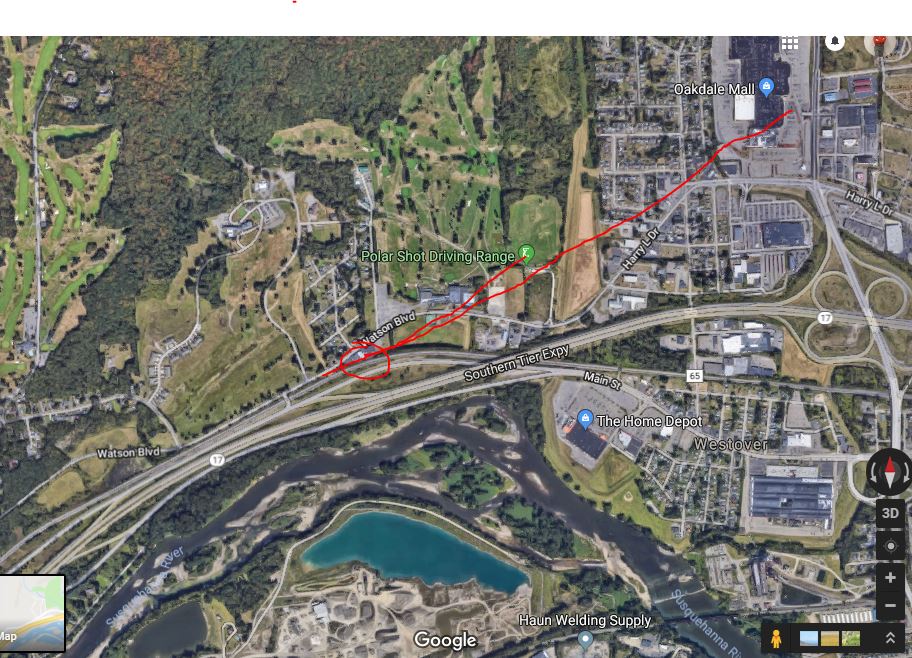
Given these problems, the TCMS recovery team decided to attempt to track the balloon along its predicted flight path by following Route 17 East. We pulled off the highway in Hancock, NY, and attempted to “find” the direction the balloon was traveling by using a directional yagi antenna and the balloon’s SSTV signal.
Erik then noticed that the SSTV system had started to produce “non-green” photos! Apparently the balloon had reached an altitude where the sun’s image saturation was less of a problem.

Around this time many amateur radio operators from other states started capturing images and uploading them to the project’s website https://reachfornearspace.com/users-post-gallery/
Unfortunately no data was generated when the balloon reached its peak altitude, but we estimate that it ascended to ~70,000 feet as the APRS GPS system started transmitting data while descending, and the first packet transmitted recorded an altitude of 69,559 feet.
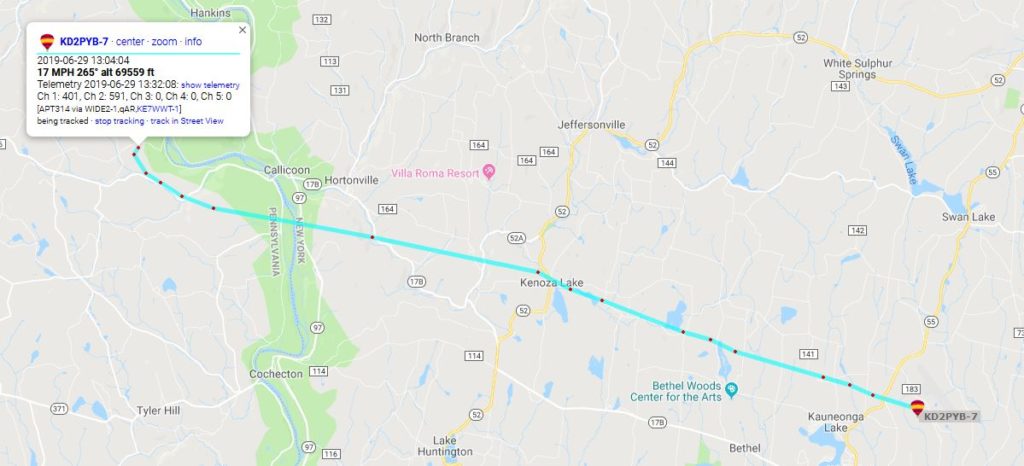
The furthest SSTV signal report came in from Cleveland, Ohio, with an estimated signal distance of ~342 miles!
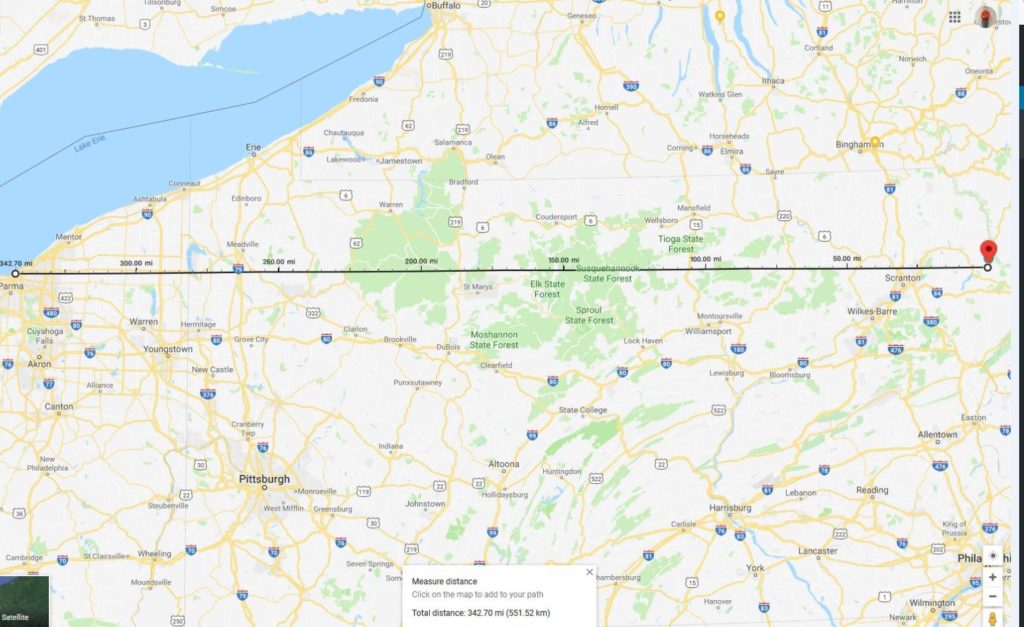
Cleveland is just barely within line-of-sight signal range of the balloon with an altitude of ~70,000 feet:
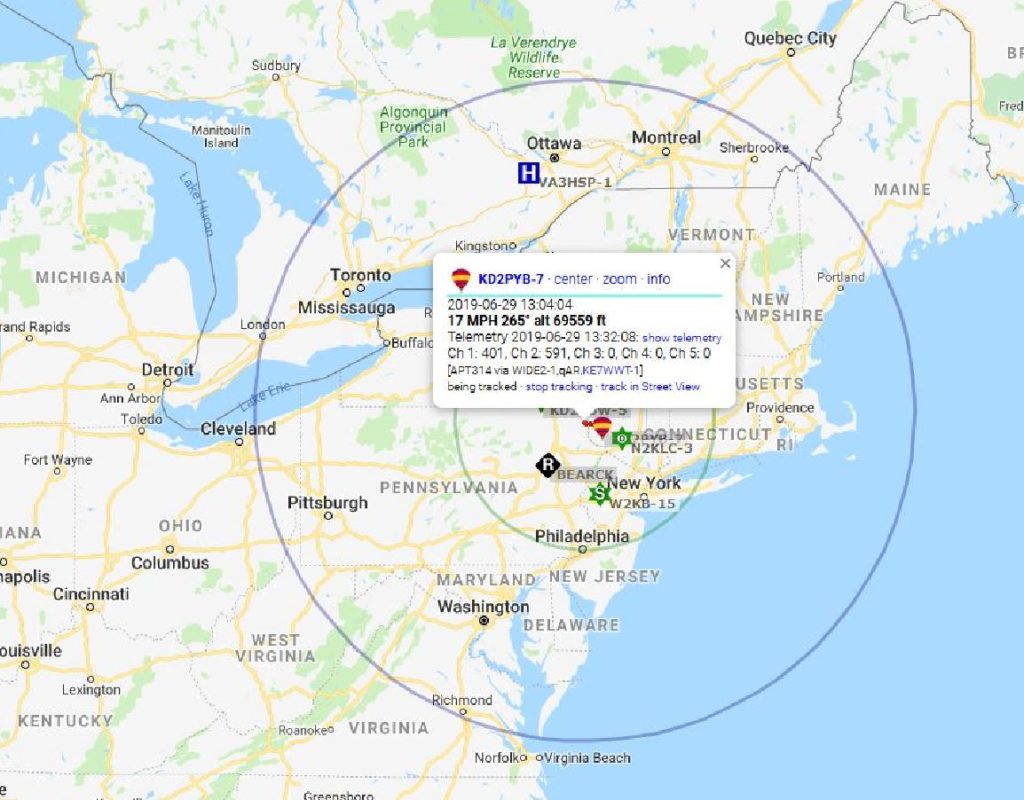
Other signal reports came from Connecticut (~111 miles), Maine (~292 miles), Maryland (~234 miles), and Rhode Island (~196 miles)!
The last APRS packet was transmitted near the Sullivan County Airport at an altitude of ~3000 feet.
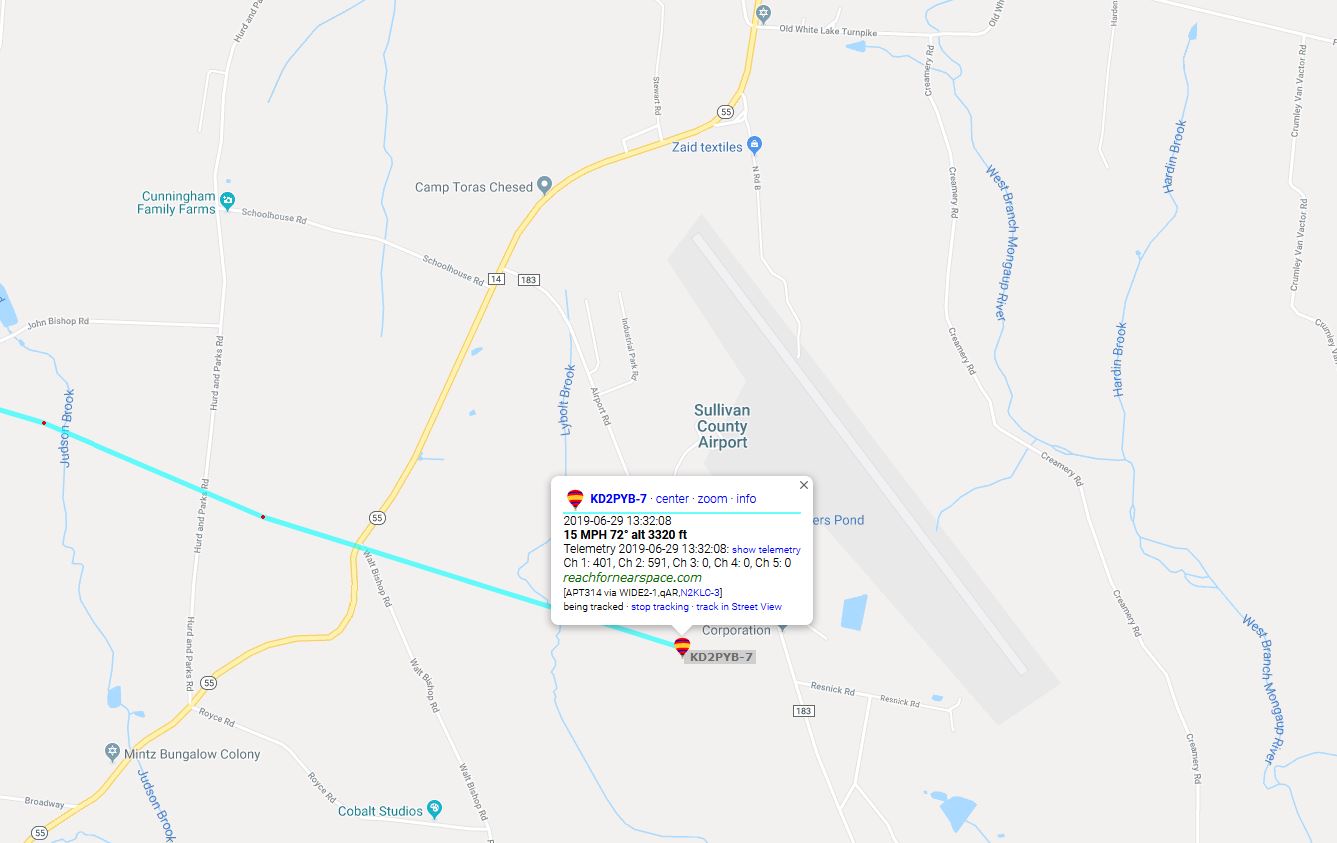
We drove to the airport and attempted to find the balloon and its payload with the help of the airport’s personnel. Because there were no local i-gates (APRS Internet Gateways) nearby, we didn’t initially have the payload’s final GPS coordinates; but using a handheld radio and the apsdroid app on my phone, I was able to receive a signal and retrieve the final GPS coordinates!
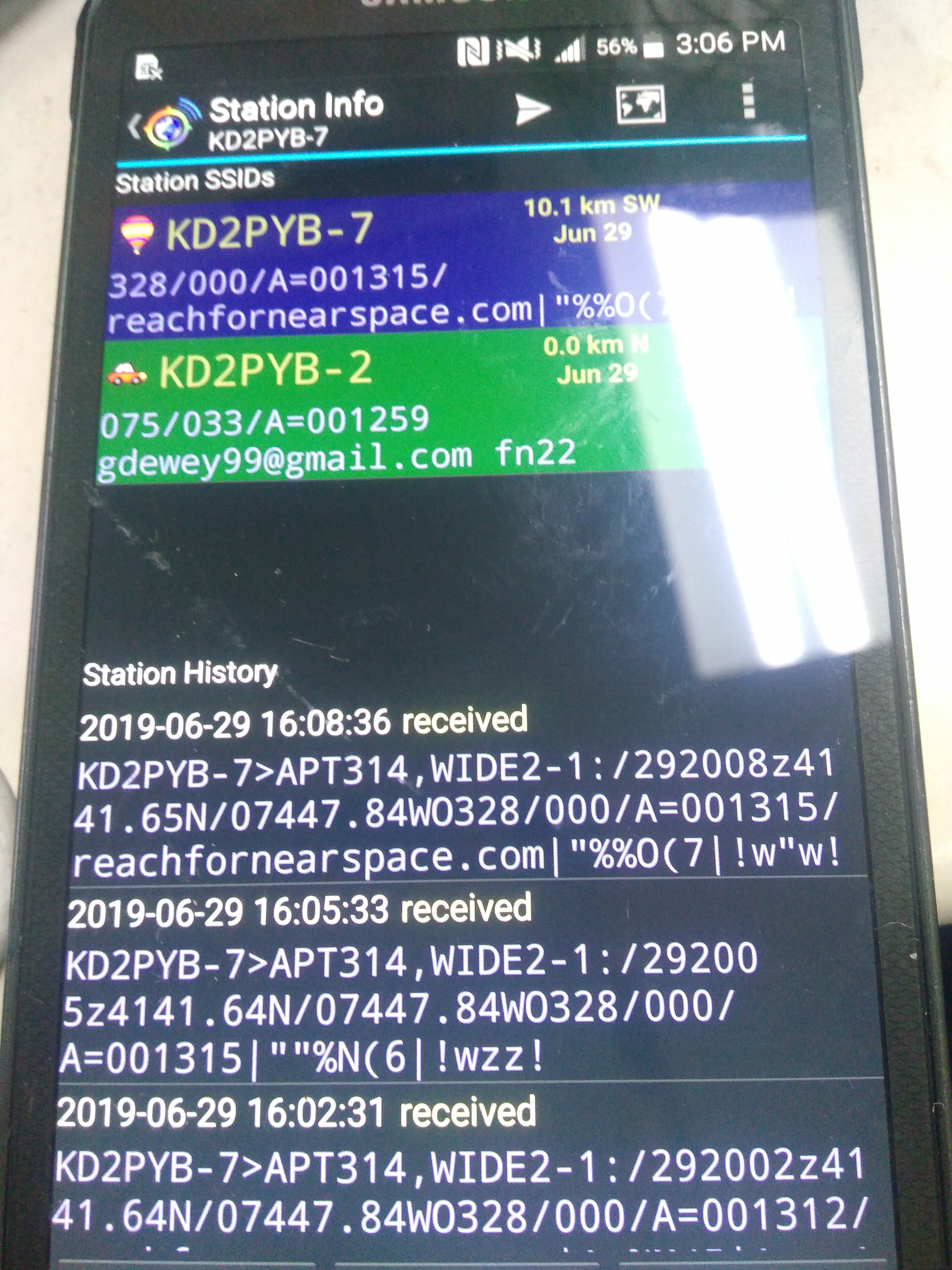
We retrieved the payload shortly afterwards; its parachute allowed all of the equipment to land without damage, and we retrieved HD video footage of the balloon’s ascent from the HD camera’s microSD card! The camera recorded in 5 minute segments, which we stitched together and uploaded to YouTube:
Here is the final video segment recorded near the peak (apogee) of the balloon’s flight; the camera shut off shortly afterwards for reasons unknown:
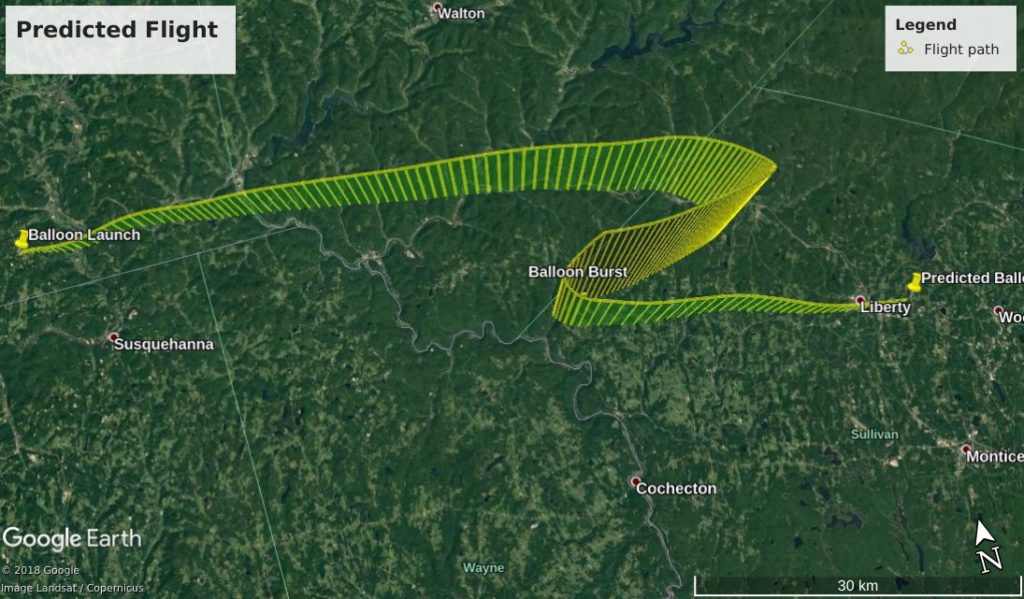
We have no APRS data for the balloon’s ascent, but we can compare the predicted vs the actual data for the balloon’s descent:
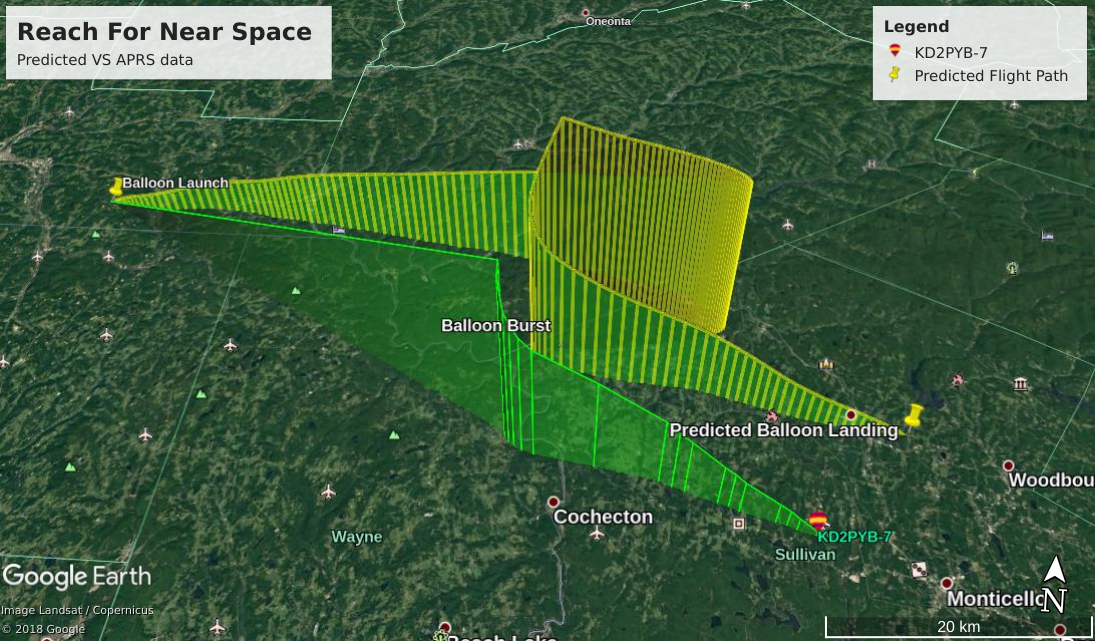
There is also no video footage for the descent, but it can be simulated by putting the APRS data into Google Earth:
Despite the problems with the APRS transmitter and SSTV camera saturation, this was a fantastic project and experience! I have learned a lot about radio, public relations, web programming and more in the process, and intend to try a similar project soon.
Special thanks to the Triple Cities Makerspace Crew for assisting me with the balloon launch and recovery, and thanks to all participating radio operators: W3AVP KB1PVH W3BAS N3CAL AC1GX N9AGC K6LPM KY1K KB3PQT N2TMS KB2BLS NP2GG N3EPY N3FWE KC9ONY WB8REI N8WAC
All photos and video footage courtesy of and property of Gary Dewey.